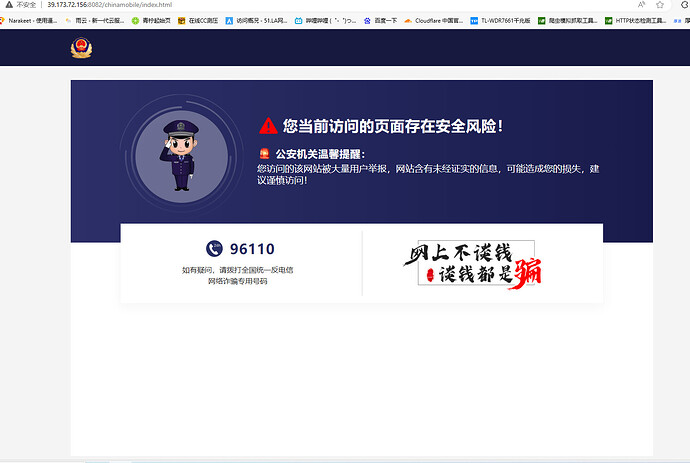
我的域名页面(https://luyii.fun)被浙江移动劫持到反诈了
itdog测试:
|移动 浙江杭州|104.21.51.35|Anycast/cloudflare.com|200|0.197s|2.007s|0.195s|--|1次 (耗时: 0.194s)
|HTTP/1.1 302 Moved Temporarily
Connection: close
Content-Length: 0
Server: Apache-Coyote/1.1
Location: http://39.173.72.156:8082/chinamobile/index.html
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 02 Mar 2024 16:00:59 GMT
Content-Type: text/html
Last-Modified: Mon, 13 Mar 2023 07:56:01 GMT
Transfer-Encoding: chunked
Connection: keep-alive
Vary: Accept-Encoding
ETag: W/"640ed711-27f4"
Content-Encoding: gzip
于是我搞了个反转跳
原理就是首次访问不会被劫持,当用户加载网页,Javascript执行保存网页到本地,并设置下次访问时从本地加载,并加入拦截转跳
项目地址: luyii-code-1/AntiChinaMoble302: 反中国移动302域名劫持 (github.com)
Github访问不了?试试DevSideCar
···劫持效果:
仅浙江移动劫持(本来电信也劫持,后来申诉解决了)